Encryption is a way of scrambling data in order to ensure only authorized parties can understand the knowledge. In technical terms, it’s the method of converting plaintext to ciphertext. In simpler terms, encryption takes readable data and alters it in order to make it appear random. Encryption requires the utilization of an encryption key, which is a group of mathematical values that both the sender and the recipient of the encrypted message can understand.
8 Basic Encryption Terms Everyone should Know
1. Hash
Once you’ve gotten your required encryption type, you may be prompted to further confirm that your data isn’t altered and is authentic and verified. For that, you would like to use hashes, they’re a one-way function that takes an outsize set of knowledge and convert them into a little standard size data. In order to achieve this you will create a single fingerprint that’s proof that your data has not been altered during different encryption levels. The result of hashing is named hash value or hash digest. If by any chance there’s a skepticsm in the data being changed or altered, you’ll always compare the original hash with the new one because two differently altered data cannot produce equivalent hashes.
If we glance at the back-end process, then hash functions when a user logins through their ID and password. The server scans for the related hash value. The password which you entered is hashed with an equivalent algorithm through which it had been encrypted. If it matches the already stored hash value then it’s valid and authenticated.
2. Digital certificate
Once you’ve identified that your encrypted information isn’t altered, it’s also necessary to spot from which source your encrypted information is coming and who will decrypt it. This is often where digital certificates are available, which also are referred to as private certificates or public-key certificates They verify the small print of the sender and receiver of the encrypted data over the web using various sorts of encryption methods. The certification authority must issue you a digital certificate. Which contains the following:
- Your name
- Certificate authority’s name
- Unique certificate serial number
- Its expiry date
- Unique private key
- Certificate authority’s digital signature
- Once your digital certificate is issued, you’ll use it as a source of verification for your various online needs.
3. Asymmetric and Symmetric
Asymmetric: This encryption operates with two keys: one public key and one private key. the general public key is shared with anyone. However, the private key must remain as a secret key because you will have to encrypt your data or message employing a public key and decrypt employing a private key. Again, imagine a situation where you’ve got put two locks on a box, one among those two locks features a passkey that anyone can have access to. However, the second key’s only with you and your lover with whom you’ve got to share the box. You can send the box to your friend through the assistance of another person. When tries to open it and only get through one lock because he has the passkey and was unable to access the second key then he will have not choice other than to deliver the box to your friend, whom with the assistance of the second key can have access to the knowledge you shared.
Symmetric: It works on one private key, therefore it’s faster than asymmetric encryption. During this encryption method, the sender must share the private key with the receiver to access the information. It is an old encryption technique which is extremely documented. Since the key’s imagined to be shared with both the sender and the receiver, it needs to be shared in a secure layer. Otherwise, the hacker has easy access to the content of the documented file you just send.
The problem with this method of encryption is in order for data to be decrypted, the key must be available. This causes two problems. The first problem is the key needs to stored securely. If an attacker were to gain access to this key they could decrypt any data that key was used to encrypt. It is common for Symmetric keys to be stored in a safe place and only accessed when required.
The next problem is if another party needs to decrypt the information. In order for this to occur, a secure channel needs to be used to transfer the key. For example, a common practice is for the key to be transferred using the telephone. A good example is season 4 of the Money Heist, where the professor and its gangs are using it.
It is better for you to see a real-life example of Symmetric encryption and how it is vulnerable.
5. IPsec
IPSec is a suite of protocols that allow secure encrypted communications between two computers over an unsecured Network IPSec. Internet Protocol Security (IPsec) may be a framework for various sorts of encryption. It helps verify different packets, which are encrypted and decrypted employing the public and a private key, within the protocol. For authentication, hash values also are added in those packets. If the sent packet is different from the received packet, then you’ll easily identify that there has been a change made during the method. IPsec can be run through two different operations.
- Tunnel mode
- Transport mode
There are two phases how internet protocol security works:
Phase one is Internet Key exchange (IKE) where both computers identify and authenticate each other. The authentication and identification is establish a security association.
Phase 2 is about creating a tunnel between the two computers where the encrypted data will be transferred to each other.
6.Virtual Private Network (VPN)
1. PPTP
Point-to-Point Tunneling Protocol (PPTP) was acquired by Microsoft and other tech companies as a framework for types of encryption. It ensures that the transmission between the VPN (Virtual Private Network) client and the VPN server is secured. It encloses the info on the network and the one that is placed inside the IP envelope, which upon every encounter are going to be treated as an IP packet. This encryption protocol is sort of out-dated now though, and it is not recommended. It is better to know what is PPTP.
2. L2TP
Layer 2 Tunneling Protocol, endorsed by Microsoft and Cisco. It is another framework for sorts of encryption which is employed in hardware-based encryption devices. Unlike PPTP, it encloses the network data twice making the entire process slower.
Also, it works with IPsec to supply secure connection and encryption. it’s built-in altogether the operating systems and VPN-cable devices lately.
8. SSTP
Secure Socket Tunneling Protocol secures the connection between the VPN client and therefore the VPN server. Hence, all the info and Point-to-Point Protocol (PPTP) traffic through the SSL channel, which passes in between is encrypted. Therefore, it’s highly secured as compared to PPTP and L2TP. The problem is, it is available on Windows (Most secure).
7. Format Preserving Encryption (FPE)
Format Preserving Encryption (FPE) may be a fairly new encryption method. It encrypts your data during a similar format. It is a type of encryption that is mostly used for crucial information like a credit card, master card, and more. It takes those 16 digit numbers and produce numbers like your card’s number.
Suppose I am going to encrypt 0045 5896 1136 4589 numbers using the FPE. The encrypted format is those numbers will be 7961 0202 8043 1689.
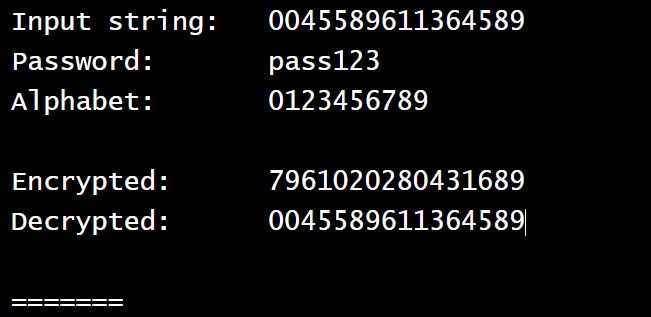
There is a website in which you can enter your information and see the result. I do not recommend you enter your crucial information there at all. Click here and it will take you there.
If you’ve got encrypted your password has 6 letters, 5 numbers, and 4 special letters, then your output is going to be a special combination of an identical format. In other words, if you employ this encryption technique, it’ll preserve the format of your plain text that’s after encryption the structure of your data will remain an equivalent.
8. SSL & Https
HTTPS (Hypertext Transfer Protocol Secure) is the secured version of HTTP which is used between a browser and a web server. Https means all communication between the browser and the webserver is encrypted. Behind https, SSL certificate plays an important role in building trust between the browser and the webserver. By definition, an SSL certificate is a web server’s digital certificate issued by a third party and it verifies the identity of a web server and its the public key.
How SSL certificate Works?
I want to connect with the YouTube web server and I want all communications with the YouTube web server are encrypted. I type in https://www.youtube.com here is what happens when I hit enter.
- step 1: my browser requests secure pages HTTPS from the YouTube web server.
- step 2: The Yahoo server sense is a public key with his SSL certificate which is digitally signed by a third party, or we call certificate authority or simply CA.
- step 3: once my browser gets the certificate it will check the issued digital signature to make sure the certificate is valid.
once the certificate is signature is verified the detailed certificate can be trusted padlock icon appears in the address bar. The padlock simply indicates that the web servers public key really belongs to the webserver, not someone else.
The secure socket layer is the third layer in the OSI Model and TCP/IP in the network model referred to as Transport Layer Security (TLS). It using port 443 which is mostly used for secure web browsing. So, you can say, Secure Sockets Layer (SSL) is Mainly developed to relate with an online server.
SSL provides encoding, message integrity using certificates, authentication during encryption, and decryption. It ensures that data is retained throughout the sharing operation. It always operates within the background.
Hypertext Transfer Protocol Secure (HTTPS) is HTTP blended with SSL. it’s a safe version of HTTP, which you see in all website’s URLs. HTTPS makes sure that your sensitive data from an internet browser to an internet site is very secured and encrypted to avoid online theft of data. It works on asymmetric key encryption that’s through private key, which is with the owner of the web site, and a public key, which is out there to everyone. So, in subsequent time you surf through an internet site, check for an ‘s’ after HTTP, to form your online browsing and data sharing secure. We have other common encryptions like plain text, ciphertext, keys, which are been used daily.

